The ability to quickly detect and respond to cyber threats isn’t now just a competitive advantage for a business — it’s a necessity. Attackers often exploit vulnerabilities within hours or days, causing significant damage: financial losses, data breaches, reputation harm, and operational downtime. Delaying response amplifies the impact. Ransomware can infect critical systems in minutes, and data exfiltrations can occur before defenses are activated.
Fast-Moving Threats: Real-World Examples
- Zero-Day Exploits: attackers target newly disclosed vulnerabilities before patches are applied. For example, the Log4j vulnerability (2021) was exploited within hours of disclosure.
- Ransomware-as-a-Service (RaaS): groups like RansomHub or LockBit exploit vulnerabilities in software (e.g., Microsoft Exchange Server flaws in 2021) within days to deploy ransomware, encrypting networks before organizations can patch.
- Credential Stuffing Attacks: automated bots test stolen credentials across platforms within hours. The Colonial Pipeline attack (2021) leveraged stolen credentials to gain access rapidly.
- Supply Chain Attacks: the SolarWinds attack (2020) exploited a vulnerability to distribute malicious updates, with attackers moving laterally across networks in days after initial compromise.
How Threat Intelligence Speeds Up Detection and Response
Threat intelligence provides actionable, real-time data on threats, enabling businesses to react faster. It includes indicators of compromise (IOCs), such as malicious IPs, domains, or file hashes, as well as context on attacker tactics, techniques, and procedures (TTPs).
By integrating this data into security operations, businesses can proactively defend against attacks. Fast detection and reaction minimize the attack’s spread, reduce recovery costs, and preserve customer trust.
Use Cases: Threat Intelligence Lookup for Prompt Defense
ANY.RUN’s Threat Intelligence Lookup is a professional search engine that navigates a crowd-powered database of malware samples and threat indicators. It works with a repository of public reports generated while using ANY.RUN’s Interactive Sandbox by 500,000 cybersecurity experts worldwide, including professional teams from 15,000 organizations.
With over 40 supported search parameters and integration of YARA and Suricata rules, TI Lookup allows users to receive quick actionable responses to quick simple requests, as well as architect complicated searches for in-depth exploration of actual and potential threats.
But let’s see how TI Lookup helps speed up detection and response.
Case 1: Immediate Verdict
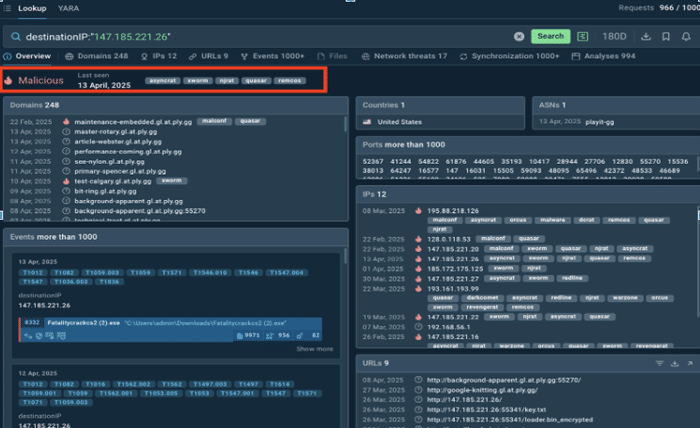
A SOC detects unusual outbound traffic to an unknown IP. To investigate, they search for the IP in TI lookup:
destinationIP:”147.185.221.26″
Results of searching for an IP in TI Lookup
So much information! But the first thing the SOC team needs to know catches their eye at once. The IP has been flagged as malicious, the IP has been spotted in most recent attacks, and the IP is associated with some of the most notorious malware. What is to be done? Block the IP and then investigate further.
Try Threat Intelligence Lookup with 50 trial requests and collect fresh IOCs on active cyber threats.
Case 2: Instant Context
After taking urgent measures and blocking the dubious IP address, we can return to the search results and look closer for additional data. There is a wealth of indicators of compromise linked to this IP, malware, and incidents analyzed by the community. TI Lookup allows to filter malicious IPs, URLs, domains, and files:
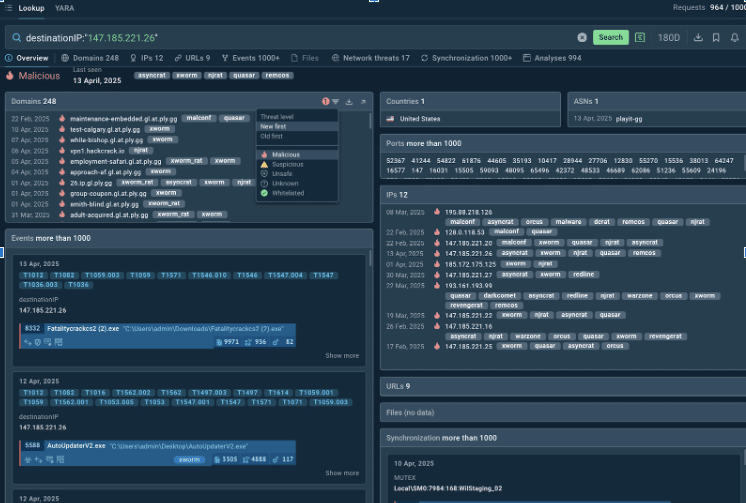
Additional indicators in the search results
Besides gathering IOCs, the search results also provide the user with details on malicious processes (in the Events tab):
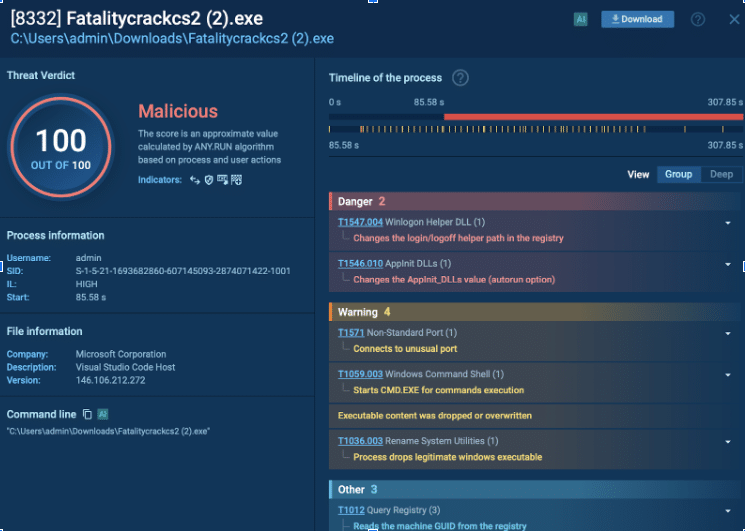
How malware attacks: detailed overview of malicious activities
With the aid of Threat Intelligence Lookup, it takes several seconds to find out whether organizations in your country are right now targeted by a specific malware:
threatName:”asyncrat” and submissionCountry:”US”
AsyncRAT fresh samples added by users of the Sandbox from the USA
This search request results in a selection of Interactive Sandbox public malware analyses submitted by users from the USA and featuring AsyncRAT: an extremely dangerous multifunctional remote access trojan. Many samples were added recently, indicating active campaigns requiring immediate action.
Case 3: Timely Updates
Automated inflow of fresh data about current threats, attacks, and campaigns is one of the most valuable resources for setting up proactive cyber defense. There are several ways to get such data from ANY.RUN’s services.
First, you can subscribe to Search Updates in Threat Intelligence Lookup. Click the bell icon in the top right corner and receive updates on your searches, keeping up with the changes in ongoing cyber attacks, collecting new IOCs and threat samples. Monitor current threat landscape to update detection rules timely.
How to get TI Lookup search updates automatically
Secondly, ANY.RUN offers Threat Intelligence Feeds: a continuously updated stream of the latest indicators of compromise. They enable SOC teams to enhance alert triage and prioritize most urgent issues, quickly detect and mitigate attacks, including emerging malware and persistent threats.
Choose a format and preferred IOCs and get a sample to test Threat Intelligence Feeds
Test a TI Feeds sample with the settings of your choice
Conclusion
In today’s threat landscape, speed is everything. The gap between a newly discovered vulnerability and the first active exploitation attempts is shrinking fast — often measured in days or even hours. Tools like Threat Intelligence Lookup allow businesses to keep pace with attackers, preemptively blocking malicious IPs, domains, and C2 servers seen in recent attacks on their industry as well as update detection rules based on emerging techniques.
Start integrating Threat Intelligence Lookup into your SOC operations to prevent threats faster than they strike




