Botnets are one of the most dangerous cyber threats facing businesses today. These networks of compromised devices, controlled remotely by cybercriminals, can be used for massive DDoS attacks, credential theft, financial fraud, and even ransomware deployment. The increasing reliance on IoT devices, cloud infrastructure, and remote access tools has made businesses even more vulnerable to botnet infections.
Understanding how botnets work and their impact on enterprise networks is important for cybersecurity teams, IT administrators, and business owners who want to prevent financial losses, operational disruptions, and reputational damage.
How Botnets Work
A botnet functions as a large-scale automated attack network, allowing hackers to take control of infected devices. Here’s how the typical infection process unfolds:
- Infection: Attackers exploit vulnerabilities in devices to inject malware, often using brute-force attacks on weak credentials or exploiting unpatched software.
- Communication: The infected device connects to a command-and-control (C2) server, waiting for instructions.
- Execution: Once activated, the botnet can carry out coordinated attacks, such as flooding networks with traffic in a DDoS attack or stealing sensitive business data.
Real-World Example of Botnet: How to Analyze It Fast
One of the most notorious botnets targeting Linux-based systems and IoT devices is Gafgyt (BASHLITE). This malware has been responsible for launching some of the largest DDoS attacks ever recorded, disrupting businesses by flooding their networks with malicious traffic.
To better understand the impact of this malware, we ran a Gafgyt sample inside ANY.RUN’s interactive Linux sandbox to observe its real-time behavior.
View analysis session with Gafgyt
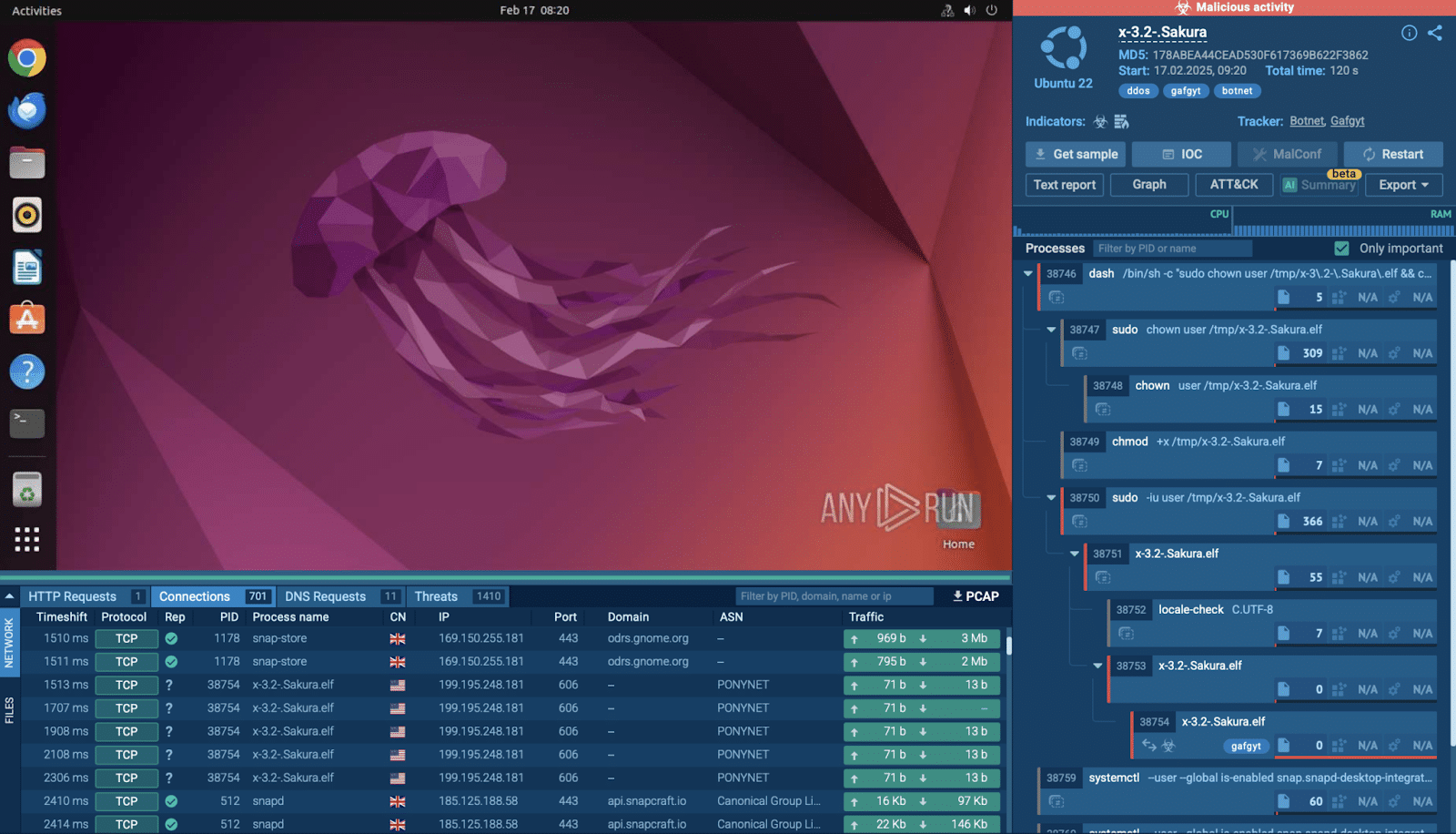
Gafgyt malware analyzed inside ANY.RUN
Inside the secure environment, we could see how the malware immediately attempted to communicate with over 700 different IP addresses, flooding the network with requests and making it difficult for legitimate traffic to pass through.
| Explore ANY.RUN’s advanced features to uncover hidden threats, enhance threat detection, and proactively defend your business against sophisticated attacks. Sign up now |
Such high-volume network activity can cripple business networks, slow down services, and cause website outages, leading to financial and reputational damage.
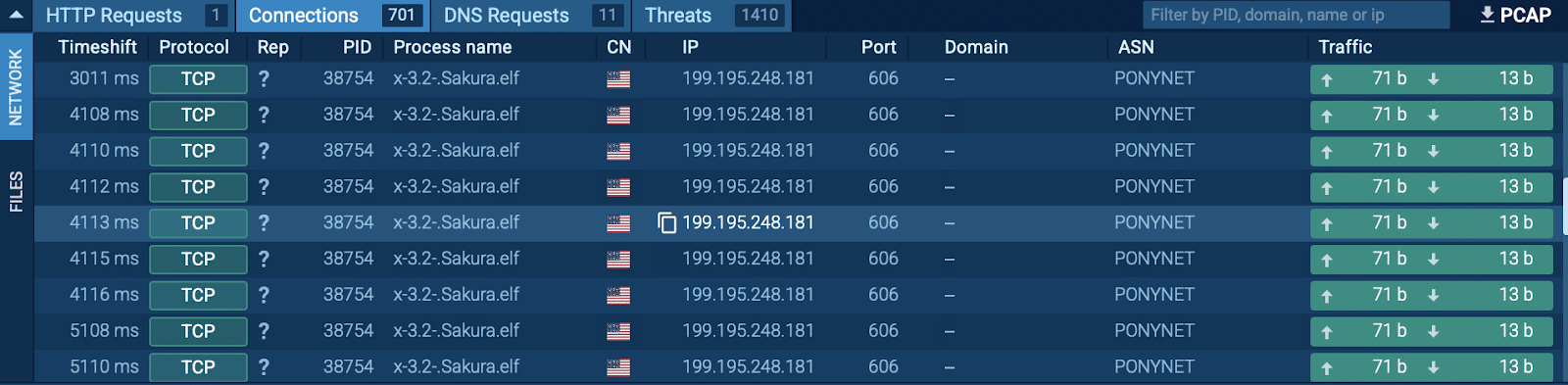
Network connections detected inside ANY.RUN Linux VM
Gafgyt established connections with command-and-control (C2) servers, sending and receiving attack instructions.
This means that once a system is infected, attackers can remotely control the compromised device, instructing it to perform various cyberattacks, such as:
- Launching DDoS attacks against competitors or financial institutions
- Harvesting corporate credentialsfor future intrusions
- Deploying ransomware payloadsor additional malware
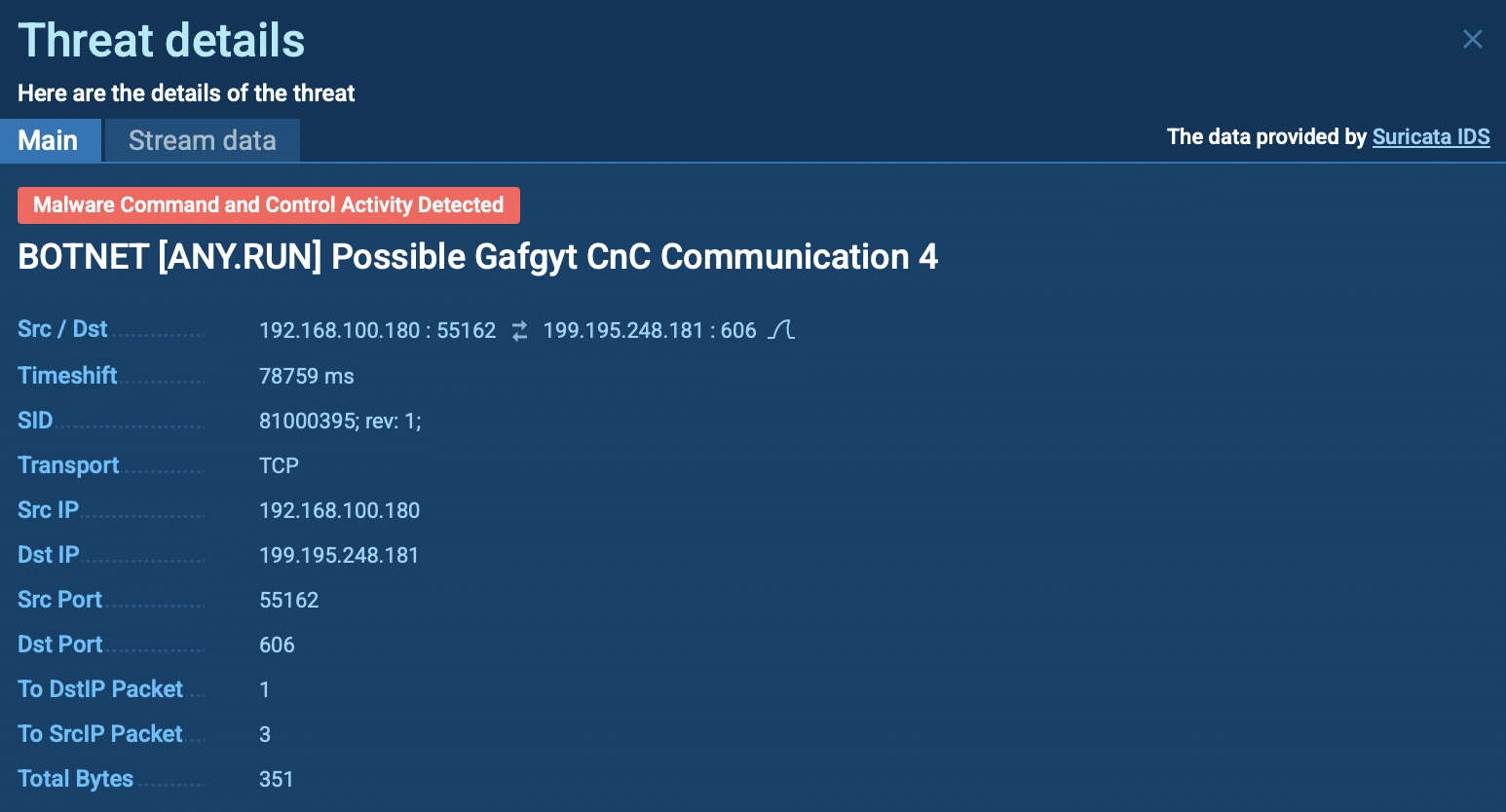
Suricata rule triggered by Gafgyt malware
The sandbox detected suspicious network behavior, flagging Gafgyt’s malicious activity through real-time Suricata rules.
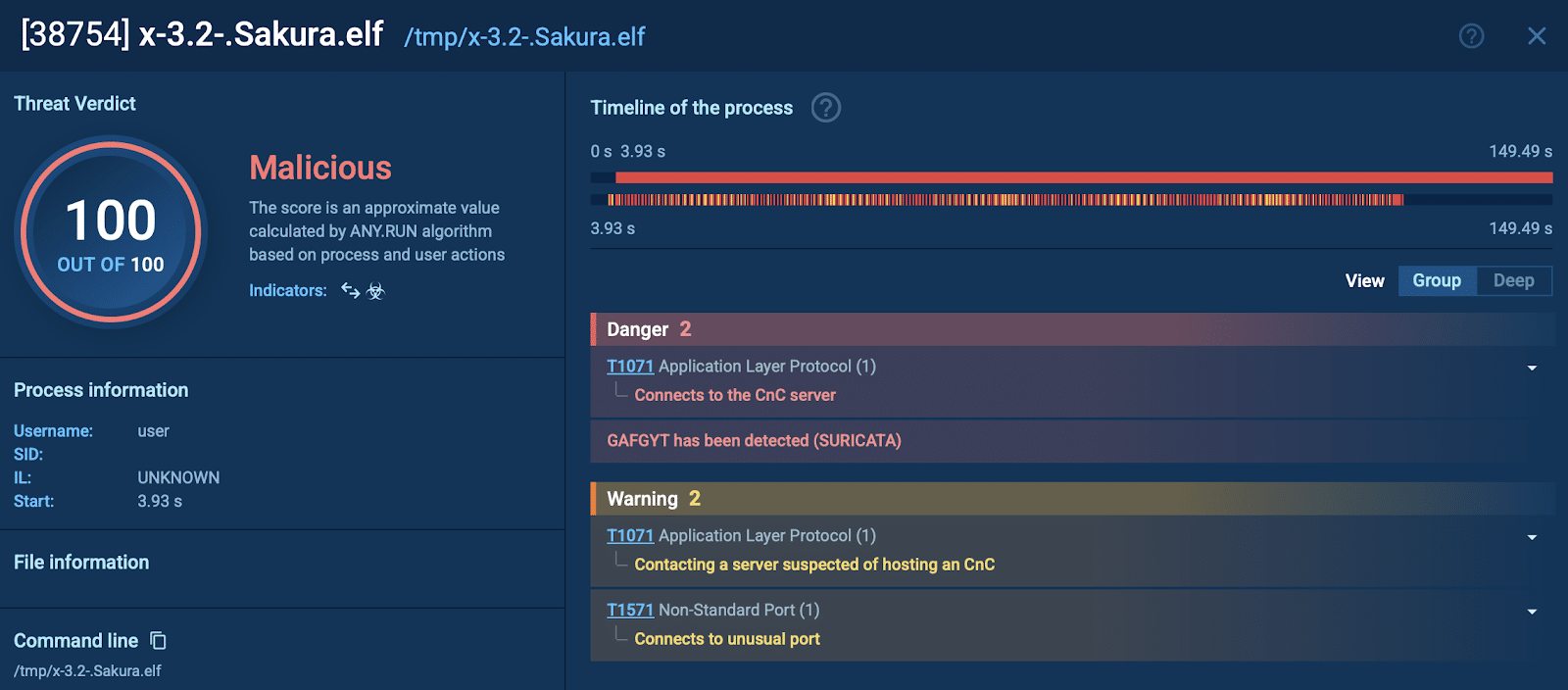
Gafgyt malware detected by ANY.RUN sandbox
The Business Impact of Botnet Attacks
As seen in real-world malware analysis, botnets operate fast. For businesses, the consequences can be severe:
- Severe disruptions: Botnets power DDoS attacks that shut down websites, cloud platforms, and critical business systems, causing downtime and revenue loss.
- Financial & compliance risks: Many botnets steal credentials, banking details, and sensitive corporate data, leading to fraud, breaches, and regulatory penalties.
- Reputation damage: A botnet-driven attack can destroy customer trust, impact brand credibility, and drive away users, investors, and partners.
- Gateway for future attacks: Botnets often serve as entry points for ransomware, espionage, or persistent threats, allowing hackers to infiltrate and exploit business networks over time.
Be Proactive Against Botnet Attacks with Smarter Defense
Botnets spread rapidly, and a delayed response can lead to significant disruptions.
Using tools like ANY.RUN’s interactive sandbox, organizations can analyze malware in a secure environment, detect threats in real time, and prevent infections before they escalate:
- Save time with fast threat analysis:Get initial results in just 10 seconds, accelerating investigations and streamlining your threat assessment process.
- Collaborate efficiently: Share findings instantly and work in real-time sessions to speed up incident response and team coordination.
- Simplify investigations: Reduce analyst workload with an intuitive interface, automated flagging, and detailed malware behavior reports.
- Gain actionable insights: Extract IOCs (Indicators of Compromise) and MITRE ATT&CK mappings for effective triage, response, and threat hunting.
- Enhance response and escalation:Improve SOC workflows by delivering structured reports from SOC Tier 1 to Tier 2 for faster and more efficient decision-making.
Sign up for ANY.RUN and try the advanced features that support real-time malware analysis, help detect botnet threats in a secure environment and simplify your threat investigation process.




